Electronic Super Joy is a platform video game created by Michael Todd. The game is available for Microsoft Windows, OS X, and Linux. The developers have announced plans to publish it on iOS. Premise Deep learning developers are gravitating toward the leading modeling frameworks, most notably, TensorFlow, MXNet, and CNTK. In addition to having well-developed ecosystems, these frameworks enable developers to compose, train, and deploy DL models in in their preferred languages, accessing functionality through simple APIs, and tapping into rich algorithm libraries and pre-defined. Aart was the lead compiler architect of automatic vectorization in the Intel® C/Fortran compilers for Windows, Linux, and Mac OS. In March 2002, Aart received the Intel Achievement Award.
- Generous Checkpoints Prototype Mac Os 7
- Generous Checkpoints Prototype Mac Os X
- Generous Checkpoints Prototype Mac Os 11
This article lists general limitations for Check Point Endpoint Security Client for macOS.
These limitations are in addition to those listed in the corresponding Known Limitations articles for each release.
Table of Contents
- Forensics
- VPN Blade
- Full Disk Encryption (FDE) Blade
- Media Encryption Blade
- Anti-Malware Blade
- URL Filtering Blade
- Installation
The following features are not supported on Check Point Endpoint Security Client for macOS:
| General Limitations |
| Push Operations are ignored for macOS client |
| Centralized Client Deployment from Software Deployment Policy is not supported |
Endpoint Client User Interface Localization is not supported |
The following configurations in Common Client Settings Policy are not supported:
|
| Telemetry data not generated |
| In order to use SideCar and Airdrop features, starting E83.20 for macOS client, you need to allow IPv6 traffic in the Endpoint Firewall policy. See sk171972 |
| Only English is supported as the interface's language. |
| The Big Sur macOS may ask users to grant access to security modules after some special activities. In such cases, follow OS directives. To avoid this, we recommend MDM management tools to predefine the desired configurations. |
| The Big Sur macOS version does not display correctly in SmartEndpoint reports. |
| If nodeJS is installed on the Mac, build directories should be excluded in SBA policy (AR/EFR and TE) to improve performance. |
| Forensics |
| The Forensics report does not show Network events. |
| Compliance Blade |
| Remediation actions are not triggered on macOS |
| Environment variables in path of checked files are not supported |
Compliance blade on macOS currently supports checks for the following Anti-Virus vendors:
|
The following compliance checks are not supported:
|
| If the default name of the compliance rule for checking if assigned blades are running is changed, i.e. cloned or edited, this rule will not be applied to the macOS Compliance blade. Then, on the server side there will be no compliance reporting (inform, warn, restrict). Client will also not go into the assumed compliance state. |
| VPN Blade |
| SCV Compliance check ('Use Compliance Blade' state should be defined in order to enforce client compliance prior to VPN connection) |
| [Not relevant for Big Sur and up] In some rare cases during the upgrade of VPN client from previous version, user may experience temporary inability to connect to VPN site. Delay may be from seconds to several minutes. To address this issue user should perform reboot of operating system. |
| A certificate for user authentication should be stored in the keychain when you use Secondary Connect. |
| Remote Access VPN clients do not support the use of a personal certificate as an authentication method if the saved certificate is on SmartCard. This is relevant for macOS 11 Big Sur. |
| Remote Access VPN clients do not support the use of personal certificates as an authentication method, if the certificate is in storage on a SmartCard. This is relevant for macOS 11 BugSur. |
| Firewall Blade |
| Disable Wireless On Lan feature is not supported |
| Application Control is not supported |
| Individual IPv6 addresses cannot be blocked. One can set 'IPv6 block all' for all IPv6 addresses. |
| Full Disk Encryption (FDE) Blade (From E80.71 LA, FDE Blade is replaced by FileVault blade) |
| Password change in FDE pre-boot is not synched to macOS |
| Smart Card login in FDE pre-boot is not supported |
| OneCheck is not supported |
| FileVault Blade |
| Only system volume is encrypted. |
| Institutional Recovery Key can only be imported once. |
| Audit logs are not generated. |
| Assigning FileVault users using SmartEndpoint is not supported. |
| User Acquisition setting 'Continue to acquire users after pre-boot has been enforced.' is not supported. |
| User Acquisition setting 'Pre-boot enforcement will begin after at least one user has been acquired after X days' is not supported. |
| Media Encryption Blade |
| Offline Mode Remote Help (MEPP / macOS Offline Access Tool does not support Remote Help) |
| Custom Encryption is not supported (Media Encryption does not support configuration of which file(s) should be encrypted) |
| Port Protection is not supported on macOS |
| CD/DVDs and storage devices connected to ports other than USB, are not supported |
| External Media that are mounted as virtual devices (Core Storage or APFS (Apple File System )) are not supported. |
| Time Machine using external media is not supported. |
| Media formatted as NTFS is not supported. |
| Media Encryption blade: Media scan - not supported. |
| Anti-Malware Blade |
| Anti-Malware Blade is not supported on macOS client. Resolved in sk165573 - Enterprise Endpoint Security E82.50 macOS Clients |
| Contextual scan - not supported (Finder does not have option for scan). Resolved in sk166955 - Enterprise Endpoint Security E83.200 macOS Clients |
| EPS-26010: Enable Web protection - not supported (always off) |
| EPS-26011: Scan Mail messages - not supported (always off) |
| EPS-26012: Signature source settings - not supported (only External Check Point Signature server setting is supported) |
| EPS-26014: Push operations:
|
| EPS-26015: Scan targets settings:
|
| EPS-26016: Configure Threat Cloud knowledge sharing - not supported |
| EPS-26017: Process exclusion - MD5 not supported |
| EPS-26059: Anti-Malware detections integration with Forensics report - not supported. |
| Anti-Ransomware |
| Backup configurations for the file types in the Anti-Ransomware policy are not enforced. |
| Backup configurations for the file size in Anti-Ransomware policy are not enforced. |
| URL Filtering Blade |
| URL Filtering is supported using Agent Chrome Browser Extension for SandBlast Agent Web Management users. |
| Capsule Docs Blade |
For list of Capsule Docs limitations, refer to sk108376 |
| Installation |
In macOS 10.13 and later, the gatekeeper requests consent from the end user before allowing to load a third party kernel extension for the first time. |
In macOS 10.13 and later, the gatekeeper warns when installing quarantined software: 'Endpoint Security installer can't be opened because the identity of the developer cannot be confirmed. Your security preferences allow installation of only apps from the App Store and identified developers.' |
In macOS 10.15 and later, the gatekeeper blocks the very first launch of third party executables that require access to user's files and folders. |
In macOS 10.15.4 and later, the gatekeeper regularly informs the end user about running 'legacy third party kernel extensions'. |
Related solutions:
If you'd like to support our preservation efforts (and this wasn't cheap), please consider donating or supporting us on Patreon. Thank you!
This is a sub-page of Proto:VVVVVV (Windows, Mac OS X, Linux).
To do:
|

If you'd like to support our preservation efforts (and this wasn't cheap), please consider donating or supporting us on Patreon. Thank you!
This is a sub-page of Proto:VVVVVV (Windows, Mac OS X, Linux).
To do:
|
This one is fully playable online here. It was made available on the developer's website sometime in June 2009. This prototype is very early in development, with several incomplete tidbits.
- 1General Differences
- 3Sprite Differences
General Differences
- There is no main menu. The game goes straight to the first room from the title screen.
- There are no cutscenes.
- The WASD keys cannot be used to move the player.
- You cannot flip by using the Up and Down arrow keys, only by pressing Z, V or SPACE.
- You cannot pause the game by pressing ENTER or ESC.
- Most of the game instructions say 'Press V' instead of 'Press ACTION'.
- Pressing R, which would normally kill the player, does nothing.
Music
None of the final game's music tracks are present in this prototype. Instead, there are two placeholder tracks, both composed by Matt Gray.
The title screen music, 'Main_music_1', which is the beginning of the Space Station Oblivion loader theme.
The level music, 'Main_music_2', which is the main theme from the Commodore 64 version of Deliverance: Stormlord II.
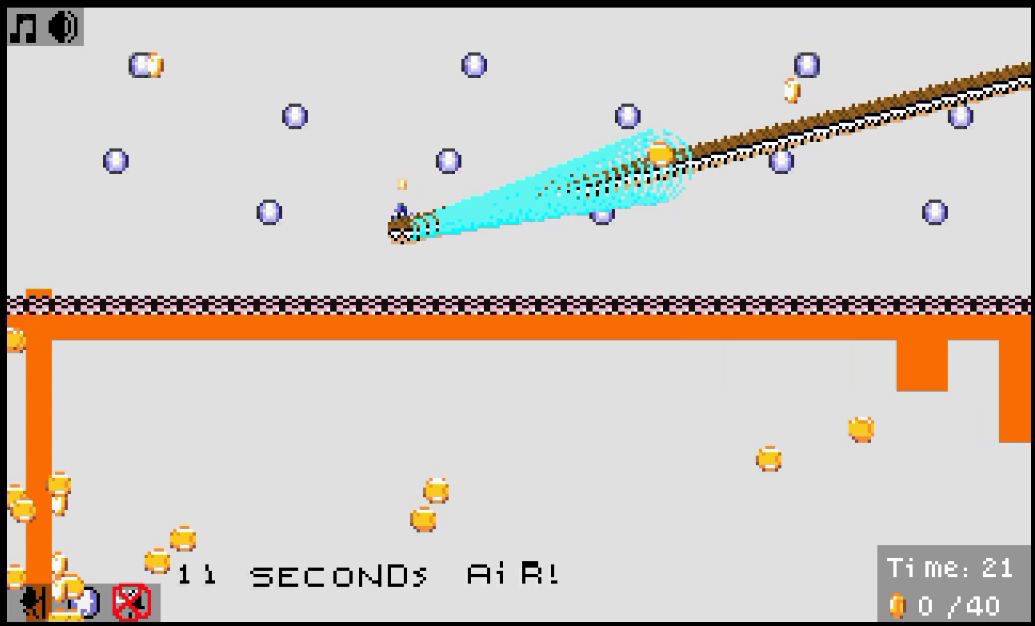
Coins
In this prototype, there are coins scattered along the level which you can collect. Their sprite would later be used for an enemy in the final game. You can still spawn them in using internal commands, but the score counter used to track the amount of coins collected was removed. Collecting a coin makes the following sound play, labeled internally as Main_ef_4:
Screens
Prototype| Final |
|---|
The screen before the title screen is much simpler.
Prototype| Final |
|---|
The title screen is completely different. Most noticeably, the title of the game is spelled VVVVVVVV (the letter V 8 times rather than 6).
Since no cutscenes are present, the game puts you directly in the first room along with the above placeholder text.
Prototype| Final |
|---|
Some of the HUD effects when collecting a trinket are missing. Additionally, collecting one does not actually pause the game, although the player is unable to move at all until they advance the text.
Map Differences
Every room has at least one difference from the final version, most commonly are the name and color palette changes. Here's the full map for the game's intro area:
Prototype| Final |
|---|
| Final |
|---|
This room's design is much simpler, with no teleporter divot in the background and a basic set of steps leading towards the next room.
Prototype| Final |
|---|
Only the room's name and color palette changed here.
Prototype| Final |
|---|
The prototype has a path downwards that was removed, along with some coins.
Prototype| Final |
|---|
This room's location was moved two rooms up and one to the left, to where the Supply Room is in this prototype. The room's layout was completely remade, making it much easier to obtain the trinket.
Prototype| Final |
|---|
Only the room's name and color palette changed here, again.
Prototype| Final |
|---|
Same as above.
Prototype| Final |
|---|
This room is quite different. The gray 'dirt' blocks are actually fall-through blocks. The path leading up was completely removed, and a checkpoint was added.
These two rooms full of coins appear directly above and below the previous room. Both of which were removed.
Prototype| Final |
|---|
This room originally had no enemies, and the main obstacle was avoiding the spikes by switching between the platforms. Not one, but two checkpoints were added.
Prototype| Final |
|---|
Some layout changes, which again make this section easier.
Prototype| Final |
|---|
Again a complete revamp, most likely to accommodate the additions of the 'Comms Relay' room to the right, as it is not present in the prototype.
Prototype| Final |
|---|
While the room's name remained the same, the layout suffered small edits, mostly to reduce the room's difficulty.
Prototype| Final |
|---|
Some coins were removed from the prototype, again.
Prototype| Final |
|---|
In the prototype, you could just move along the platform at the top and collect the trinket. Some walls were later added to prevent that. The coins became extinct, like usual.
This room has been completely removed from the final version. It appears between the previous two rooms. The two platforms move left and right, but using them can be tricky as the player doesn't actually move along with the platforms.
Prototype| Final |
|---|
This Super Mario Land 2: 6 Golden Coins reference was sadly removed, coins included. If the player dies, the disappearing platform does not respawn. You must leave the room and come back for it to reappear.
Prototype| Final |
|---|
The bus in here is significantly smaller in the prototype. There is no path on the bottom part of the room as well.
Prototype| Final |
|---|
There is no checkpoint on the right side of the room, and there are no grids in the background.
Prototype| Final |
|---|
The path in the middle was removed, again.
Prototype| Final |
|---|
This evil set of spikes at the bottom was removed, much to the comfort of many gamers.
These rooms are either completely absent in the final version, or so different there's no way to even compare them. After following the path upwards, the prototype ends with the following screen:
Sprite Differences
Checkpoints
Prototype| Final |
|---|
The checkpoints in this prototype appear to be in a hexagonal-shape and have an S in them instead of a C.
Death Sprite
Prototype| Final |
|---|
Two pixels from his eyes are filled in rather than one in the final.
Bus
Prototype| Final |
|---|
Dragon ball z: run! mac os. The wheels are more visible in the prototype and makes it look more like a bus. Additionally, the bus in the prototype uses four frames, while the final uses two.
Fall-through Tiles
Mechanics Test| VVVVVVVV Prototype |
|---|
The fall-through platforms from the previous prototype are still here. Only the block the player touches will disappear, making the noise above, labeled internally as 'Main_ef_6'. Previously, these would only break when the player landed on them, not when they walked into it from either side, but this feature has been removed.
Sound Differences
Generous Checkpoints Prototype Mac Os 7
Prototype| Final |
|---|
The sound played when collecting a trinket is different.
VVVVVVVV Prototype (GOG version)
There's a different version of this prototype, distributed alongside the Mechanics Test. It is almost identical to the one described above, except:
Generous Checkpoints Prototype Mac Os X
- There's no music at all in the game.
- You can change the amount of horizontal acceleration from 0.5 to 1.4 by pressing the keys 0 through 9 on the keyboard. The game starts with 1.1 by default.
| To do: Are there no other changes? |
